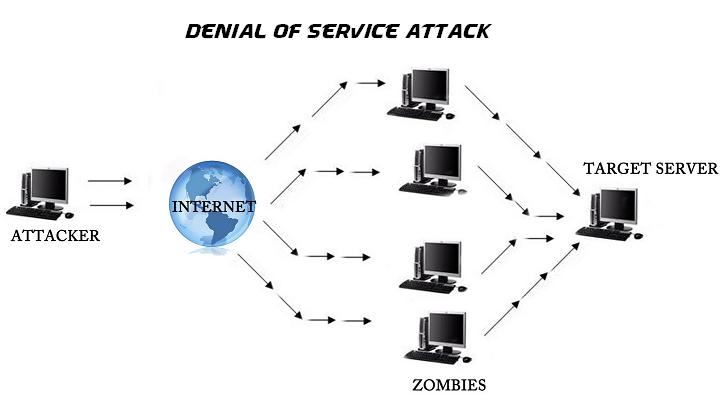
One of the most destructive Web-based attacks a server can face is a distributed denial of service (DDoS) attack. Unfortunately, this sort of attack has become extremely prevalent in recent years, and very little can be done to totally stop it. Attackers will use multiple tactics when targeting servers. Lately, we have seem a resurgence in the use of DNS amplification while sending DDoS attacks. However, a few steps can be taken to minimize the risk of your DNS server being use to be part of such attacks and to protect your DNS server from becoming unresponsive as a result of such an attack.
How DNS amplification DDoS Attacks Work
For how effective they can be, DDoS attacks are actually quite simple. The perpetrators query name servers from thousands of computers that have been infected and converted into slave systems. However, instead of using the actual IP address of each querying computer, the target’s IP address is spoofed and sent in its place. As part of the attack, each query instigates a response that is larger than usual in order to maximize the damage.
One reason that DDoS attacks have been able to succeed begins with the implementation of EDNS0, which is a series of DNS extensions that allow DNS messages to be up to 4,096 bytes in size even though most queries and responses are no larger than 100 bytes. In addition, DNS security extensions (DNSSEC) have made it a simple matter to store large digital signatures and encryption keys in responses.
When a DDoS attack is triggered, thousands of computers begin to rapidly send DNS queries with the spoofed IP address. This forces your server to use its entire bandwidth allotment sending responses to these requests, which means legitimate traffic cannot be received.
Monitoring Your Server For DDos Activities

Commonly, the first step in protecting your DNS server from DDoS attacks is to monitor the server so that you know when an attack is occurring. Many administrators do not have a clue as to their average query rates and could never recognize an attack for what it is. Although several methods and outside software can be used for monitoring purposes, it is really as simply as using the built-in statistics from BIND. You can configure a standard interval for the BIND name server to send you its statistics, which include your query rate. Keep in mind that since DNS use UDP, other services using UDP(such as SNMP, NTP, etc.) can also be exploited into amplification attacks.
Distribute Your DNS Servers
 After you have your server set to monitor for DDoS attacks, you can help prevent them by configuring the Internet-facing systems on your server. These configurations include the name servers that you use, your switches and routers, your Internet connections and firewalls. Instead of limiting yourself to a single, authoritative, external name server, you may want to consider using a broad range of name servers from around the world. This will stop attacks coming from a single area or that primarily use a single, weak DNS server.
After you have your server set to monitor for DDoS attacks, you can help prevent them by configuring the Internet-facing systems on your server. These configurations include the name servers that you use, your switches and routers, your Internet connections and firewalls. Instead of limiting yourself to a single, authoritative, external name server, you may want to consider using a broad range of name servers from around the world. This will stop attacks coming from a single area or that primarily use a single, weak DNS server.
One way to easily distribute your DNS servers is to use Anycast, which allows multiple servers, including name servers, to share IP addresses. This permits you to route your traffic through two or more different channels instead of only one. Many hosting providers and other cloud-based companies offer Anycast services for a nominal charge, and several options are available, including the following:
• Anycast IP addresses can be configured into the network.
• Software can be implemented to support host-based routing.
• Name servers can be set to listen to DNS queries through Anycast IP addresses.
• Loopback interfaces can be established that include Anycast addresses.
Overprovision Your Server
You can also overprovision your server’s infrastructure to handle large numbers of queries. However, some DDoS attacks can exceed 100 Gbps of bandwidth, which can be very expensive to provision. The positive side of overprovisioning is that your server will be ready to handle increased traffic should your business and online presence grow.
Use High Availability
Because DNS servers are critical to most online businesses and organizations, servers should be configured as a high-availability (HA) pair. A sudden overload that causes one DNS server to slow or fail can be set to trigger a standby server to take over the task of receiving queries and sending responses.
Set Response Rate Limits
Response rate limits can be configured to help prevent DDoS attacks. Response rates can be limited by both the source IP address and the destination IP address. By limiting source addresses, only so many requests can be accepted in a given time period, and by limiting destination addresses, you can shut down an attack before it hits your server in force.
Protecting your DNS servers
 In order to minimize the chances of being part of a DNS amplification attack, there is one simple step that you can achieve on your DNS server to prevent it. It is important to disable the feature that allows your DNS server to answer to recursive queries. The first thing to do is to check if your DNS server is able to resolve a dig or a NS lookup of a domain name on your DNS server. To do so, in a terminal or a CMD, type :
In order to minimize the chances of being part of a DNS amplification attack, there is one simple step that you can achieve on your DNS server to prevent it. It is important to disable the feature that allows your DNS server to answer to recursive queries. The first thing to do is to check if your DNS server is able to resolve a dig or a NS lookup of a domain name on your DNS server. To do so, in a terminal or a CMD, type :
Using Dig
dig @yourdnsserver.com www.domainexample.com
Using NS lookup
nslookup
> server yourdnsserver.com
> www.domainexample.com
Dig answer example
$ dig @yourdnsserver.com www.domainexample.com
; <<>> DiG 9.8.3-P1 <<>> @yourdnsserver.com www.domainexample.com
; (1 server found)
;; global options: +cmd
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 34294
;; flags: qr aa rd; QUERY: 1, ANSWER: 1, AUTHORITY: 2, ADDITIONAL: 2
NS lookup answer example :
Non-authoritative answer:
Name: www.domainexample.com
Address: 8.8.8.8
In both cases, if an IP is returned for www.domainexample.com, the DNS server is vulnerable.
Next thing is to disable the features on your DNS server. Here’s how you can do it on Windows :
Run this command in a cmd:
dnscmd . /Config /NoRecursion 1
Or follow this procedure:
Start | Administrative Tools | DNS (DNS manager)
Right click DNS server |
Properties |
Advanced |
Server options |
Disable recursion -> Yes, OK
For Linux :
Add this to the “options” section of /etc/named.conf :
recursion no;
additional-from-auth no;
additional-from-cache no;
Then restart named so that it will use the new secure options:
/etc/init.d/named restart
OR
If your DNS server is used only by the machine on which you are running it, you can block external queries by performing the following steps:
(Before implementing any new firewall rules, make sure that the following iptables rules are applicable in your case.)
iptables -A INPUT -p udp -m udp –dport 53 -i ! lo -j DROP
These iptables firewall rules will prohibit ANY queries to a non-recursive DNS:
iptables -A INPUT -p udp -m udp –dport 53
-m string –hex-string “|0000ff0001|” –algo bm –from 48 –to 65535
-m recent –set –name anydnsquery –rsource
iptables -A INPUT -p udp -m udp –dport 53
-m string –hex-string “|0000ff0001|” –algo bm –from 48 –to 65535
-m recent –rcheck –seconds 60 –hitcount 5 –name anydnsquery –rsource
-j DROP
If you for some reason have to run an open DNS resolver, you can limit rate limit the rate at which you will accept queries:
iptables -A INPUT -p udp –dport 53 -m hashlimit
–hashlimit-name DNS –hashlimit-above 20/second –hashlimit-mode srcip
–hashlimit-burst 100 –hashlimit-srcmask 28 -j DROP
There’s no real way to fully protect yourself against a DDos attack as your server needs to respond to certain query. It’s not possible to block every request that comes from external sources as your server might be useless. Though, you can protect your system against usual DDos attacks like DNS amplification attack. It is also possible to reroute the heavy requests that are made from a third-party client.

 Call us at 1-888-GTCOMM1
Call us at 1-888-GTCOMM1