How to Protect Yourself Against Ransomware
We operate in a digital world filled with different malware circling through cyberspace, but ransomware is not just your run-of-the-mill malware. Ransomware is more devious and more sophisticated than other pieces of malware; ransomware blocks the target’s access to their system files, demanding a ransom to get the decryption key or to get the system unlocked.
Encryption ransomware works by encoding the system files while calling for ransom, often in Bitcoin, to get the decryption key. If payment is not made within a specified time, the data may be lost forever.
Locking ransomware works by locking the target out of their operating system, meaning the desktop and any files cannot be accessed. The files are not encrypted here, but a ransom is still required to unlock the system.
There are more insidious versions of ransomware that can infect key portions of the operating system, such as the Master Boot Record (MBR). The MBR is the part of the hard drive that allows the system to boot up, so disabling this process removes access to the system.
Encryption ransomware, often called crypto-ransomware, is the most commonly encountered ransomware.
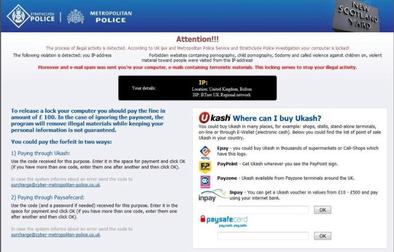
Key Characteristics of Ransomware
While ransomware is a type of malware, it features some characteristics that make it more advanced than other malware. Some of the common characteristics that ransomware shares include:
• Ransomware utilizes unbreakable encryption algorithms
• It can encrypt all types of files and data
• They can also scramble and alter file names
• File extensions may be changed or added
• A ransom message will be displayed on boot or login
• Payments are often requested in Bitcoin
• The ransom may contain a time requirement or time limit
• The infected systems may become part of a botnet
• Other devices on the local network can be infected
• It employs unique methods to hide from anti-virus software
How to Protect Yourself Against Ransomware
Protecting against ransomware often requires more robust protection than a standard anti-virus software can offer, though companies are working to enhance their products in these areas. However, there are ways that you can protect against ransomware and the adverse effects of an incident.
Harden the Operating System
Hardening your operating system against these attacks starts with running an updated system with current updates installed. On Windows-based operating systems, for instance, it’s important to install critical updates when prompted. Additionally, avoiding an end of life (EOL) operating system is crucial for security and safety.
EOL operating systems are systems that have reached the end of their support period from the provider. Windows XP was a popular operating system that recently reached EOL, which means that it will no longer receive system updates or critical patches. Running an EOL system opens you up to vulnerability and exploitation, especially if new vulnerabilities are discovered; the provider will no longer repair those issues.
If an EOL system must be used, it’s recommended that any Server Message Block 1 (SMB1) or Common Internet File System (CIFS) be disabled to reduce the potential for different ransomware files to gain access to the system. This article from Microsoft goes into greater detail about the steps necessary, based on the operating system used.
Some EOL systems from Windows include Windows XP, Windows Vista, Windows 8, Windows Server 2003, and Windows Server 2008.
Currently supported systems include Windows 7 SP1, Windows 8.1, Windows 10, Windows Server 2008 R2, Windows Server 2012, Windows Server 2012 R2, and Windows Server 2016.
Implement and Update an Anti-Malware Program
Commonly referred to as anti-virus programs, anti-malware programs are geared towards protecting your system from a variety of threats. Ransomware typically does not fall into the traditional virus category, due to the sophistication of the program, so a more robust option may be necessary.
Several companies, including AVG and Malwarebytes, are working to create usable solutions that address more than just common viruses, Trojans, and worms. However, when you’re looking for a solution, there are few things to consider:
• Does the anti-malware program offer real-time protection?
• Are definition updates installed automatically or manually?
• What types of malware does this program identify?
• Does the solution include data encryption or a firewall?
It’s important to compare your anti-malware options before making a decision since you need a solution that meets or exceeds your expectations and your needs. What will work for a single home computer will not necessarily work for a network of 10 small business computers.
Additional Steps to Take on Your System
Mentioned previously, a firewall is an excellent way to reduce the potential for ransomware infection. Firewalls work by preventing unauthorized access to the network; firewalls may be hardware or software form, or there are combination firewalls available. These solutions will prevent your private network from being accessed from the outside, which is especially helpful with intranets.
Additionally, taking steps to back up your data can help you recover if a ransomware attack is successful. It’s recommended that backups be stored in two places, one in digital form in the cloud and one on an external drive. This will allow you to get your data back even if there is a ransomware infection.
Disabling port 445 is another step to take for your system, which disables traffic to the internet and from the internet through this port. While your system will have many port options, 445 is commonly used by different malware due to the unsecured nature of the port. It’s important to block 445 only where needed since it can be necessary within the Windows environment for successful communication between applications or services. This article by Microsoft details how to set up a port 445 block.
Another suggestion to reduce ransomware attacks is to use a Linux-based or UNIX-based system, such as Ubuntu, ElementaryOS, or even the popular MacOS. While all operating systems can be vulnerable when they are not updated or patched correctly, these systems are known for having a different approach regarding security updates than Windows systems. Additionally, the open source nature of Linux systems allows users to identify and patch vulnerabilities much quicker.
Be Cautious Online
Hardening your operating system and making changes to how your system works are essential to protect against ransomware, but being careful online is crucial to continued protection.
A common way ransomware can infect a system is when email attachments are opened from unknown senders or sources. Ransomware files could be attached to seemingly innocent files, which means you should never open an attachment unless you were expecting it. Even then, it’s important to confirm the file is clean and free of malware.
You can easily verify the security of a file and the integrity of it by using a service like VirusTotal, which works by analyzing the file to detect any suspicious malware. VirusTotal uses over 60 different scanners to check the file, providing a reasonable assurance of security.
If you utilize a Remote Desktop setup, changing the default port the Remote Desktop listens through is important. This program is used to access your desktop from a remote location, so changing the default port to a less commonly used port can make it harder for malicious individuals to gain easy access to your desktop.
Conclusion
Protecting your system and your files against Ransomware is not a one-size-fits-all solution, and it’s a constant battle to keep your data secure. However, there are simple ways to make the target on your system smaller while making a recovery easier.
Running an actively updated or patched operating system, instead of an end of life system, ensures you’re receiving timely security updates from the provider. Additionally, a robust anti-malware program can help detect unusual activity before it causes a problem. Also, blocking port 445 and changing default ports for remote desktop programs can make it harder for ransomware to find a way into the system.
Finally, it’s important to only open or download files from trusted sources, using a service like VirusTotal when you’re not sure about the file’s security. Also, make sure to create a local backup and a digital, cloud backup of your data. The physical backup should be stored separate from your system, reducing the risk of damage or ransomware infection.

 Call us at 1-888-GTCOMM1
Call us at 1-888-GTCOMM1



