Linux Firewall Introduction
As cyber-crimes and cyber-attacks continue to increase, the need for cyber-security has never been more important. That’s why it has become extremely important to protect our servers as well as our web assets. How should we proceed to establish a secure environment? What are some of the options open to us? There are many ways to ensure the security of your dedicated server, and in this blog entry, we will discuss firewalls, their usage and configuration and which may be best for different applications.
What’s a firewall ?
A firewall is a security component that allows and restricts access to specific networks and ports. It is generally accompanied by routing capabilities, increasing its functionality and making it a very popular security solution. There are two types of firewalls: software and hardware. Software firewalls tend to be cheap (or free) and easily available while hardware firewalls are more expensive, full-featured and their capabilities (Throughput, packets per second, etc.) have been measured and are guaranteed to the user. While their additional features are different, their primary functions remain the same: restricting access to your network or dedicated server.

A software firewall is an application that is installed on a server which controls and restricts network access to the machine. It’s generally setup on a specific server where other applications are located. Because of that, a software firewall will sometimes take up resources on a server, increasing the load of that machine. Both Linux and Windows generally come with their own software firewall, while several other third-party options exist as well. One feature that strongly distinguishes a hardware firewall from a software firewall is that a hardware firewall runs on its own proprietary hardware. It does not take up resources from your server when it’s running. It is its own entity. This means that most people will plug their hardware firewall upstream from their server. Additionally, since it often has more than one port, more than one server may be plugged to it. This way, it can protect several servers, or even several networks on bigger setup. By that point though, it behaves more like a router than a simple firewall.
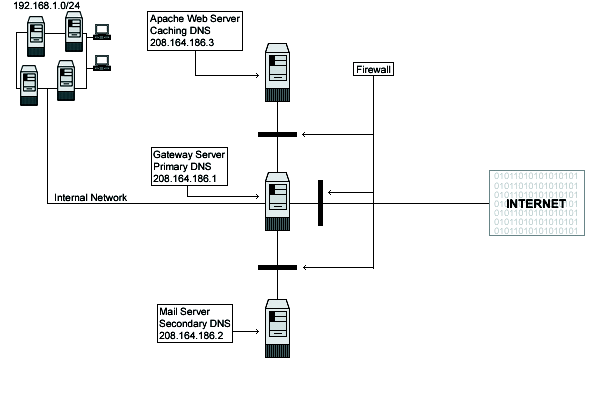
(Click on the image to enlarge the firewall protected server’s schema)It is possible to recreate such a setup using a software firewall. However, it requires adding another computer in front of your server, installing several network interface cards on this computer and then setting up a routing configuration so that the software firewall may route packets correctly. In that sense, the hardware firewall is more beginner-friendly, as it’s generally setup out of the box and only requires a firewall configuration.
I’ve been saying since the beginning of this article that firewalls restrict access to the server, but how do they do this? We first need to understand that an un-configured firewall is useless. It will not block anything by default. This also means that it’s impossible to open a port on an un-configured firewall since nothing is blocked by default. When you want to block something, you need to specify a source (can be a wildcard), a destination (can also be a wildcard), a protocol or port, depending on if you want to block access to a specific service or application on the server and “accept” or “deny” access, depending on if you want to authorize the traffic or deny it access to the server. Once that rule is set, the firewall will analyze every packet of data which goes through the server and reject everything that it is set to reject.
How to add a rule on a Linux firewall ?
To illustrate what a firewall rule might look like, let us simulate a firewall rule on port 22(SSH default port on most Linux distribution). Here is an example of an iptables rule:
iptables -I INPUT -i eth0 -p tcp –dport 22 -j ACCEPT
The –I flag add the rule at the top of the list, so it’s the first rule taken into account when iptables is running. INPUT designate the series of rules which affect incoming connections to the server. “–i eth0” specifies the interface this rule applies to. “-p tcp” is the type of network protocol. “—dport 22” is the destination port where the service we want to control listen to. “-j ACCEPT” specifies whether packets should be accepted or rejected. So, what this example does is that it allows traffic through the firewall for port 22, the SSH service port. Of course, firewall rules are not exactly easy to generate from scratch, and we highly recommend to have a system administrator write them into your firewall.
Other options also exist to increase the amount of security features a software firewall like iptables can provide. For example, there is the CSF plugin, which increases iptables functionalities greatly. CSF adds country blocking and better IP block management capabilities to iptables, among other things. It can also be fully integrated into cPanel, so that you can manage your software firewall from the GUI. Here’s how to install it on most linux distributions.
 That being said, while the core base features might be similar, a hardware firewall such a Cisco ASA series will provide you more feature such as IPsec VPN, Native High-Availability firewall setup, VLAN setup, etc. while guaranteeing its throughput capabilities.
That being said, while the core base features might be similar, a hardware firewall such a Cisco ASA series will provide you more feature such as IPsec VPN, Native High-Availability firewall setup, VLAN setup, etc. while guaranteeing its throughput capabilities.
That is all for this introduction to firewalls. In the next article, we will look at Cisco ASA firewall. That article will be followed by another piece that goes into more details about iptables.

 Call us at 1-888-GTCOMM1
Call us at 1-888-GTCOMM1