Let’s Encrypt is a free Certificate Authority that provides a free SSL certificates for your domain. Let’s Encrypt provides a Certbot tool to obtain and install TLS/SSL certificates automatically on both Apache and Nginx web server. The certificate is valid for 90 days. So you will need to renew it before it expired. Let’s Encrypt is a nonprofit certificate authority managed by the Internet Security Research Group. Its main aims is to create a more secure and privacy-respecting Web by adopting HTTPS.
In this tutorial, we will learn how to install and secure a LAMP server with a free Let’s Encrypt SSL on Debian 10.
Requirements
- A server running Debian 10
- A valid domain name pointed to your server IP
- Root access to the server
LAMP Server Installation
Let’s start with installing LAMP server on your server:
apt-get install Apache2 mariadb-server php php-cli php-common libapache2-mod-php wget -y
Once all the packages are installed, start Apache and MariaDB service and enable them to start on system reboot with the following command:
systemctl start apache2
systemctl enable apache2
systemctl start mariadb
systemctl enable mariadb
Create Virtual Host for your Domain
Next, you will need to create a virtual host server block for your domain. You can create it with the following command:
nano /etc/apache2/sites-available/blog.fictivedomain.conf
Add the following lines:
<VirtualHost *:80>
ServerName blog.fictivedomain.com
ServerAdmin admin@fictivedomain.com
DocumentRoot /var/www/html
ErrorLog ${APACHE_LOG_DIR}/error.log
CustomLog ${APACHE_LOG_DIR}/access.log combined
</VirtualHost>
Save and close the file, when you are finished. Then, enable Apache virtual host with the following command:
a2ensite blog.fictivedomain.com.conf
Install and Configure Let’s Encrypt
First, you will need to install Certbot tool to secure your web server with Let’s Encrypt. By default, the latest version of Certbot is not available in the Debian 10 default repository.
You can add the Certbot repository with the following command:
apt-get install software-properties-common
add-apt-repository ppa:certbot/certbot
Next, update the repository and install Certbot with the following command:
apt-get update -y
apt-get install certbot python-certbot-apache -y
Next, you will need to create a well-known.conf file for Let’s Encrypt to validate your domain.
To do so, first create a .well-known directory and give proper permissions with the following commands:
mkdir -p /var/lib/letsencrypt/.well-known
chgrp www-data /var/lib/letsencrypt
chmod g+s /var/lib/letsencrypt
Next, create a well-known.conf file with the following command:
nano /etc/apache2/conf-available/well-known.conf
Add the following lines:
<Directory "/var/lib/letsencrypt/">
AllowOverride None
Options MultiViews Indexes SymLinksIfOwnerMatch IncludesNoExec
Require method GET POST OPTIONS
</Directory>
Save and close the file. Then, enable the required modules with the following command:
a2enmod ssl
a2enmod headers
a2enmod http2
a2enconf well-known
Finally, restart Apache service to apply all the configuration changes:
systemctl restart apache2
Now, run the following command to install and configure your certificate for domain blog.fictivedomain.com:
certbot --apache -d blog.fictivedomain.com
You will be asked to enter an email address and agree to the terms of service.
Saving debug log to /var/log/letsencrypt/letsencrypt.log Plugins selected: Authenticator apache, Installer apache Enter email address (used for urgent renewal and security notices) (Enter 'c' to cancel): admin@fictivedomain.com - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - Please read the Terms of Service at https://letsencrypt.org/documents/LE-SA-v1.2-November-15-2017.pdf. You must agree in order to register with the ACME server at https://acme-v02.api.letsencrypt.org/directory - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - (A)gree/(C)ancel: A - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - Would you be willing to share your email address with the Electronic Frontier Foundation, a founding partner of the Let's Encrypt project and the non-profit organization that develops Certbot? We'd like to send you email about our work encrypting the web, EFF news, campaigns, and ways to support digital freedom. - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - (Y)es/(N)o: Y Obtaining a new certificate Performing the following challenges: http-01 challenge for blog.fictivedomain.com Enabled Apache rewrite module Waiting for verification... Cleaning up challenges Created an SSL vhost at /etc/apache2/sites-available/blog.fictivedomain.com-le-ssl.conf Deploying Certificate to VirtualHost /etc/apache2/sites-available/blog.fictivedomain.com-le-ssl.conf Enabling available site: /etc/apache2/sites-available/blog.fictivedomain.com-le-ssl.conf
If it’s successful, certbot will ask to choose whether or not to redirect HTTP traffic to HTTPS. Choose appropriate option then hit ENTER. Once the certificates are installed successfully, you should see the following output:
Please choose whether or not to redirect HTTP traffic to HTTPS, removing HTTP access. - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - 1: No redirect - Make no further changes to the webserver configuration. 2: Redirect - Make all requests redirect to secure HTTPS access. Choose this for new sites, or if you're confident your site works on HTTPS. You can undo this change by editing your web server's configuration. - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - Select the appropriate number [1-2] then [enter] (press 'c' to cancel): 2 Enabled Apache rewrite module Redirecting vhost in /etc/apache2/sites-enabled/blog. fictivedomain.com.conf to ssl vhost in /etc/apache2/sites-available/blog. fictivedomain.com-le-ssl.conf - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - Congratulations! You have successfully enabled https://blog. fictivedomain.com You should test your configuration at: https://www.ssllabs.com/ssltest/analyze.html?d=blog. fictivedomain.com - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - IMPORTANT NOTES: - Congratulations! Your certificate and chain have been saved at: /etc/letsencrypt/live/blog.fictivedomain.com/fullchain.pem Your key file has been saved at: /etc/letsencrypt/live/blog.fictivedomain.com/privkey.pem Your cert will expire on 2019-10-22. To obtain a new or tweaked version of this certificate in the future, simply run certbot again with the "certonly" option. To non-interactively renew *all* of your certificates, run "certbot renew" - Your account credentials have been saved in your Certbot configuration directory at /etc/letsencrypt. You should make a secure backup of this folder now. This configuration directory will also contain certificates and private keys obtained by Certbot so making regular backups of this folder is ideal. - If you like Certbot, please consider supporting our work by: Donating to ISRG / Let's Encrypt: https://letsencrypt.org/donate Donating to EFF: https://eff.org/donate-le
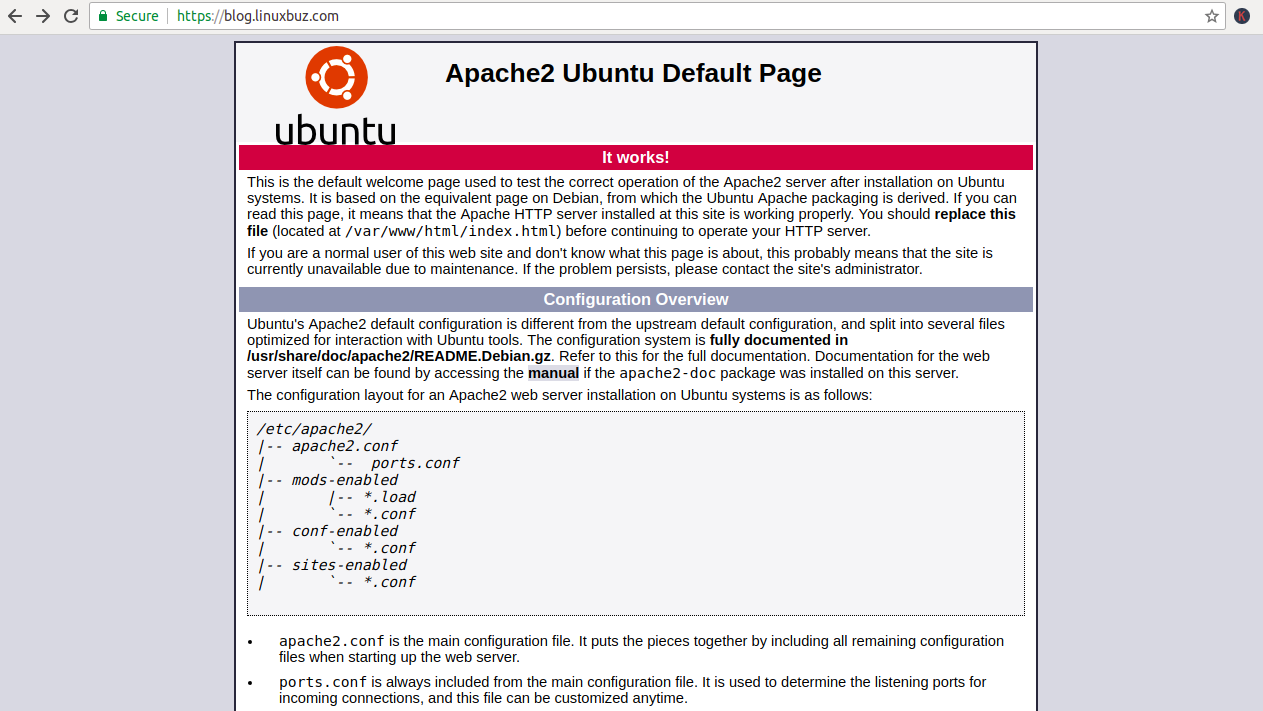
Now, open your web browser and type the URL https://blog.fictivedomain.com. You should that the site is properly secured, usually with a green lock icon, meaning that you successfully installed your free Let’s Encrypt SSL:
Setting Up Auto Renewal
Let’s Encrypt free SSL certificates are valid for 90 days. So, you will need to set up a cron job to auto-renew SSL certificate. It is safe to create a cron job that runs every week or even every day.
If you want to renew the SSL certificate manually, run the following command:
certbot renew --dry-run
You can setup cron job to auto-renew SSL certificate by editing following file:
crontab -e
Add the following line:
52 10 * * * root /usr/bin/certbot renew >/dev/null 2>&1
Save and close the file, when you are finished.
Conclusion
In this tutorial, we have learned how to install a free SSL on Apache web server with Let’s Encrypt. I hope you can now easily secure your web server with Let’s Encrypt.

 Call us at 1-888-GTCOMM1
Call us at 1-888-GTCOMM1





