Difference Between FTP and SFTP
When running a Windows or Linux server, it becomes necessary to implement a system for file transfers through a network. However, several protocols are available, and it is up to you to decide which is best for your particular server and situation. The oldest and most commonly used network protocol for uploading and downloading files is the file transfer protocol (FTP), but a newer protocol using advanced technology, Secure Shell File Transfer Protocol (SFTP) is becoming increasingly popular because of its security features. If you are having trouble choosing which protocol to use, the following guide may help you decide between FTP and SFTP.
 FTP Overview
FTP Overview
FTP is the earliest protocol for file transfers still in use today. It was first proposed to the Internet Engineering Task Force (IETF) in Request for Comments (RFC) 114 in April 1971, and it was fully developed into the protocol still used today in October 1985.
FTP is a protocol used for exchanging data over private or public networks, such as local area networks (LANs) or the Internet. In order to accomplish the task, data is sent through two different channels: the command channel and the data channel.
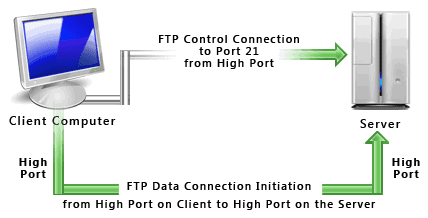
In most instances, the command channel runs through server port 21, and its purpose is to establish client connections by handling simple commands from an FTP client and server. Examples of such commands include USER and PASS, which identify and authenticate particular FTP users. This channel remains open until the connection is closed manually with the QUIT command or by the server.
The FTP data channel uses an on-demand system to listen to ports on the server in passive mode or on the FTP client in active mode. It is this channel that is responsible for the exchange of data. When a transfer is initiated, the channel opens, and it closes when the transfer is finished.
Setting up FTP on a server is simple and can be accomplished with one of several FTP clients to make the process even easier. A few of the most popular clients that can be used with Windows and Linux servers are FileZilla, FireFTP, gFTP and NcFTP. Through the client, you can establish ports, protocols, users, remote access, connections, limits and other relevant settings. Commands can then be given through a GUI or command line.
 SFTP Overview
SFTP Overview
SFTP, not to be confused with FTPS, has become a popular alternative to FTP because it provides secure access to accounts that are on remote systems. Instead of using dual channels, SFTP uses SSH protocol to transfer commands and data in the form of uniquely formatted packets through a single connection. Port 22 is usually used by SFTP for both inbound and outbound connections.
Although most of the FTP client (like Filezilla) are able to establish a SFTP connection without requiring the server to have an SSH tunnel, here’s how to set the tunnel up. Establishing an SSH tunnel is usually done through an SFTP client, such as PuTTY or OpenSSH. Tunneling allows for multiplex connections through forwarded TCP ports, and it can be used in much the same way as a virtual private network (VPN). To create an SSH tunnel through OpenSSH, you can use a command such as the following:
ssh -2 -N -f -L 1234:localhost:25 user@example.example.com
In the above command, the -2 forces the program to use SSH version 2, the –N opens a tunnel with no command, -f indicates that SSH is to run in the background and –L tells the system that it is a local tunnel in the format of localport:remotehost:remoteport.
Establishing an SSH tunnel through PuTTY is very similar to doing so through OpenSSH. The following command format can be used:
putty.exe server1 –L 1234:server2:23
Other commands can also be entered, such as -N and -f.
File Transfer Security
 When it comes to security, FTP is very risky. While FTP can be set to require a password, the username and password are transmitted unencrypted through the command channel. Anyone intercepting this unencrypted transmission would be able to download sensitive data or upload malware to the server.
When it comes to security, FTP is very risky. While FTP can be set to require a password, the username and password are transmitted unencrypted through the command channel. Anyone intercepting this unencrypted transmission would be able to download sensitive data or upload malware to the server.
SFTP, on the other hand, encrypts both the commands and the data that are transferred through the SSH channel via a cypher and encryption keys. Newer SFTP clients support 256-bit encryption, but many users will find 128-bit encryption sufficient.

 Call us at 1-888-GTCOMM1
Call us at 1-888-GTCOMM1